How to Quickly Automate a Secure Cloud with AWS-native Services
This is a recap of a recent expert webinar featuring Lahav Savir, CTO and Co-Founder at AllCloud; Himanshu Verma, WW Security Specialist at AWS; Alon Diamant-Cohen, Security Specialist at AllCloud; and Lior Pollack, CTO at Praxis.
During the webinar, which you can watch here, we provided an overview of AWS Security Services, addressed the top security challenges facing AWS customers in 2021, discussed how to quickly automate a secure cloud environment using AWS-native Services, and explored the importance of evolving to a cloud-native security strategy.
Himanshu Verma, WW Security Specialist at AWS – An Overview of AWS Security Services
Himanshu Verma provided an overview of the value proposition of AWS security services and the way security decisions impact business outcomes, such as time to market and user experience. Since development is fundamentally dependent on secure environments, Himanshu argued, AWS security services have been designed to get “security out of the way” as quickly as possible.
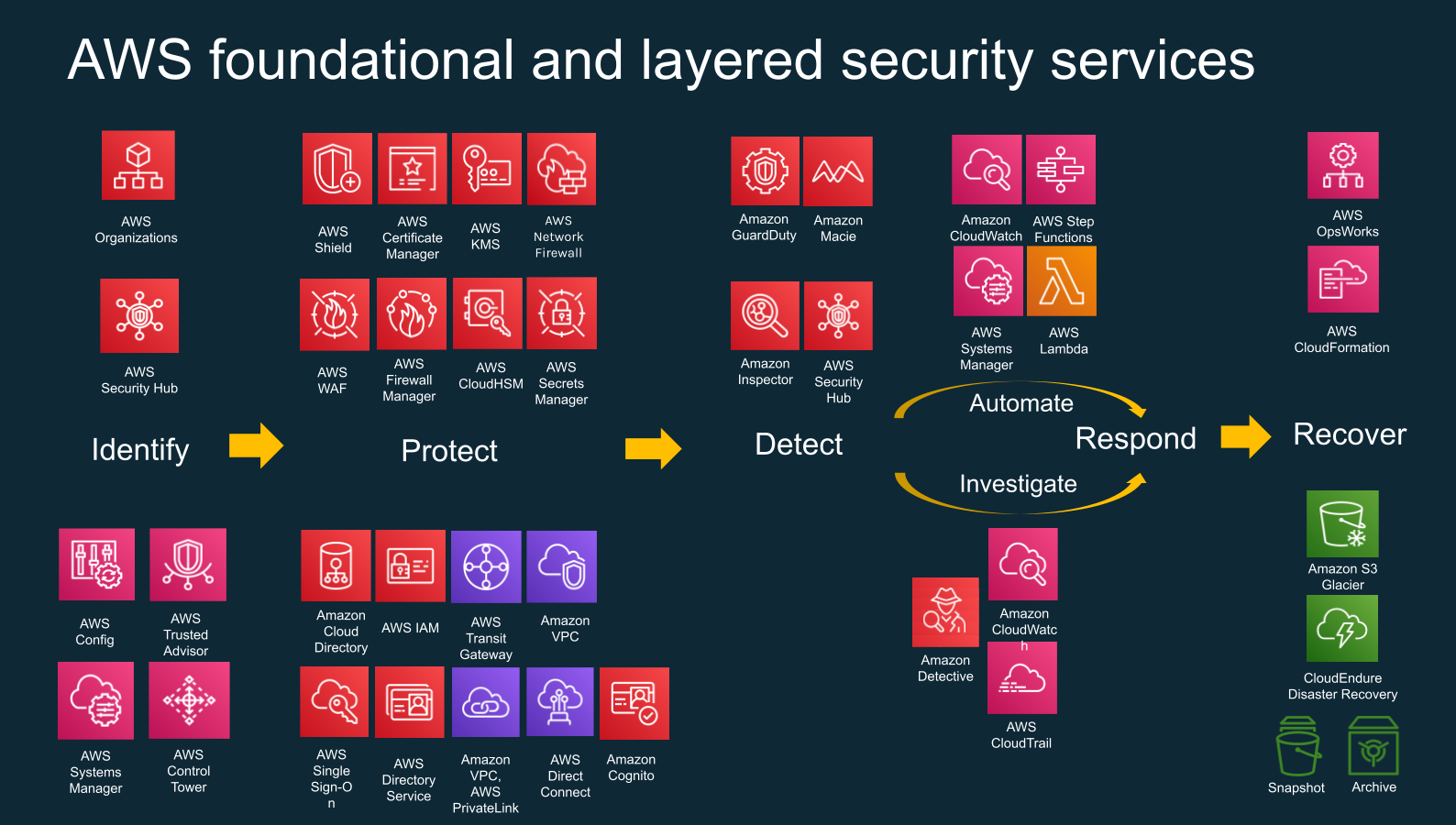
Himanshu further elaborated on best practices to secure cloud environments and how AWS security services overlap with the NIST cybersecurity framework. In this context, Himanshu explained how security best practices have changed in the recent decade and evolved from an “egg” to an “onion” approach. While an egg has one hard shell which separates it from its environment, an onion is structured in layers. Correspondingly, modern security approaches call for security measures within all environment layers, rather than “one strong wall”, shielding the perimeter from the outside world.
Additionally, Himanshu provided an overview of the architecture of an AWS account and how a multi-account strategy helps companies to grow securely while efficiently segregating resources.
Alon Diamant-Cohen, Security Specialist at AllCloud – The Top Security Challenges Facing AWS Customers in 2021
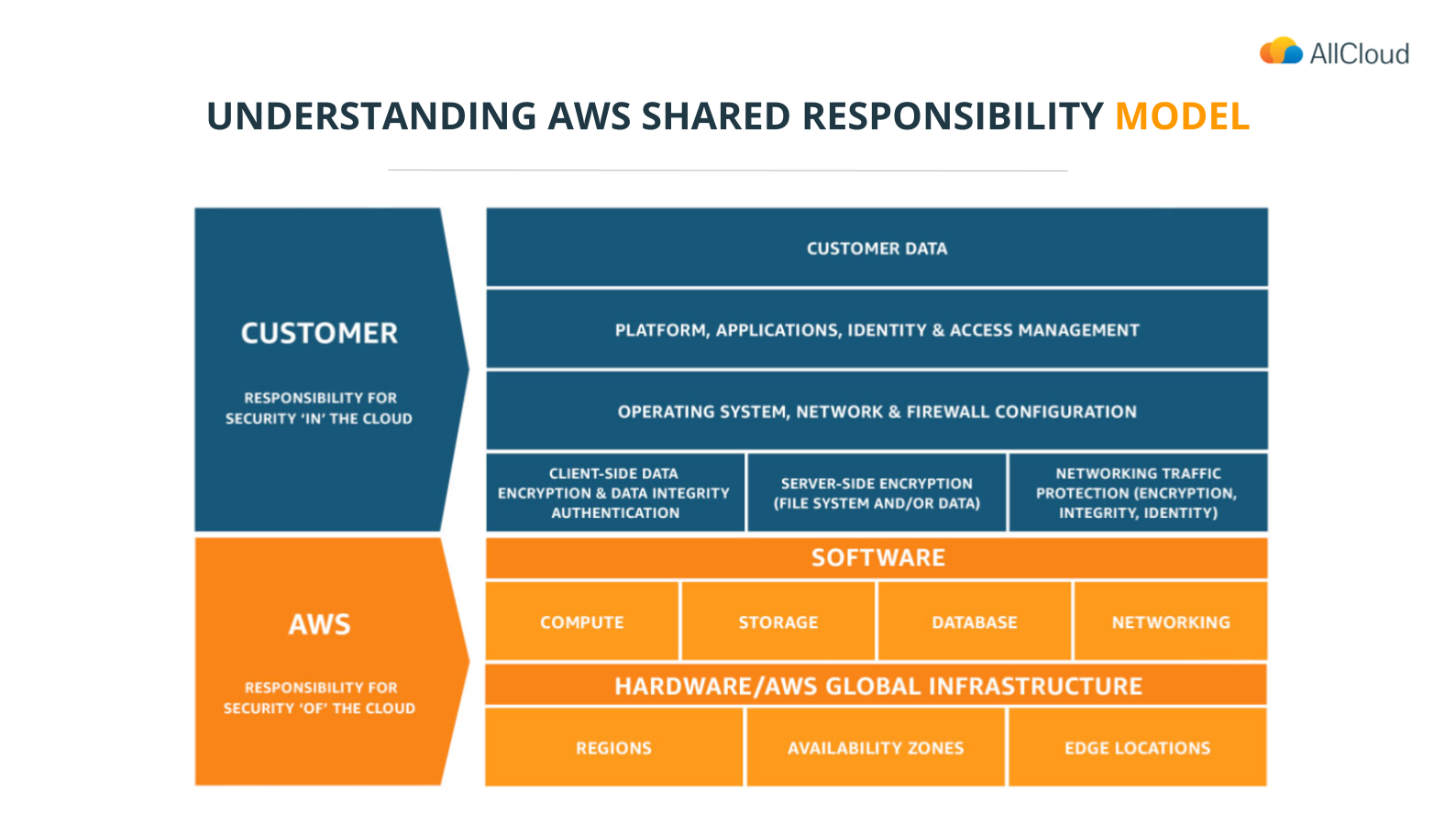
Alon started his presentation by presenting the CSA’s list of top security risks in 2021 and stressed that half of them arise from customers misunderstanding the AWS Shared Responsibility Model.
The Shared Responsibility Model dictates that while AWS provides Security of the Cloud, customers are responsible for Security in the Cloud. This means that AWS is responsible for protecting the infrastructure that runs all of the services offered in the AWS Cloud. This infrastructure is composed of hardware, software, and facilities that run AWS cloud services. The customer, on the other hand, is responsible for configuring their environment correctly, managing access privileges, detecting and responding to unauthorized access attempts.
As an example, Alon examined the Capital One data breach case study. In the Capital One case, simple misconfigurations, such as making an S3 bucket public and adding unnecessary permissions to a role led to catastrophic outcomes.
To conclude, Alon shared his recipe for cloud security success which among other things includes ingredients such as adherence to the Least Privilege Principle, a Defense-in-Depth approach and reducing public configurations to a bare minimum.
Lahav Savir, CTO at AllCloud – How to Quickly Automate a Secure Cloud Environment Using AWS-native Services
To demonstrate how AllCloud recommends quickly automate a secure cloud environment, Lahav introduced AllCloud’s Next-Generation Landing Zone solution(NGLZ).
The NGLZ is a fully automated enterprise-scale, governance, and security solution. It is built to configure and update a multi-account, multi-region AWS organization, based on AWS cloud-native services. The NGLZ implements AWS security best practices using services such as Control Tower, KMS, AWS Config, GuardDuty, Security Hub, Inspector, and Service Catalog. The solution bridges any gaps left by AWS Control Tower to provide a single end-to-end framework for security orchestration and visibility that meets the most stringent security, governance and compliance standards.
Lahav reviewed the solutions covered by the NGLZ and the benefits of using it, such as:
- A fully automated configuration for AWS Organization’s security and governance policies, guardrails, and monitors.
- The enforcement of integrated security policies, governance, and compliance regulations.
- The definition of multiple environments, using different policies and guardrails.
- Quick recognition and response to any intrusion and the mitigation of risks and damages.
- Usage of corporate credentials to access AWS resources within a hybrid environment.
- A single view into an entire AWS Organization’s security events and notifications.
Lior Pollack, CTO at Praxis – The Importance of Evolving to a Cloud-native Security Strategy
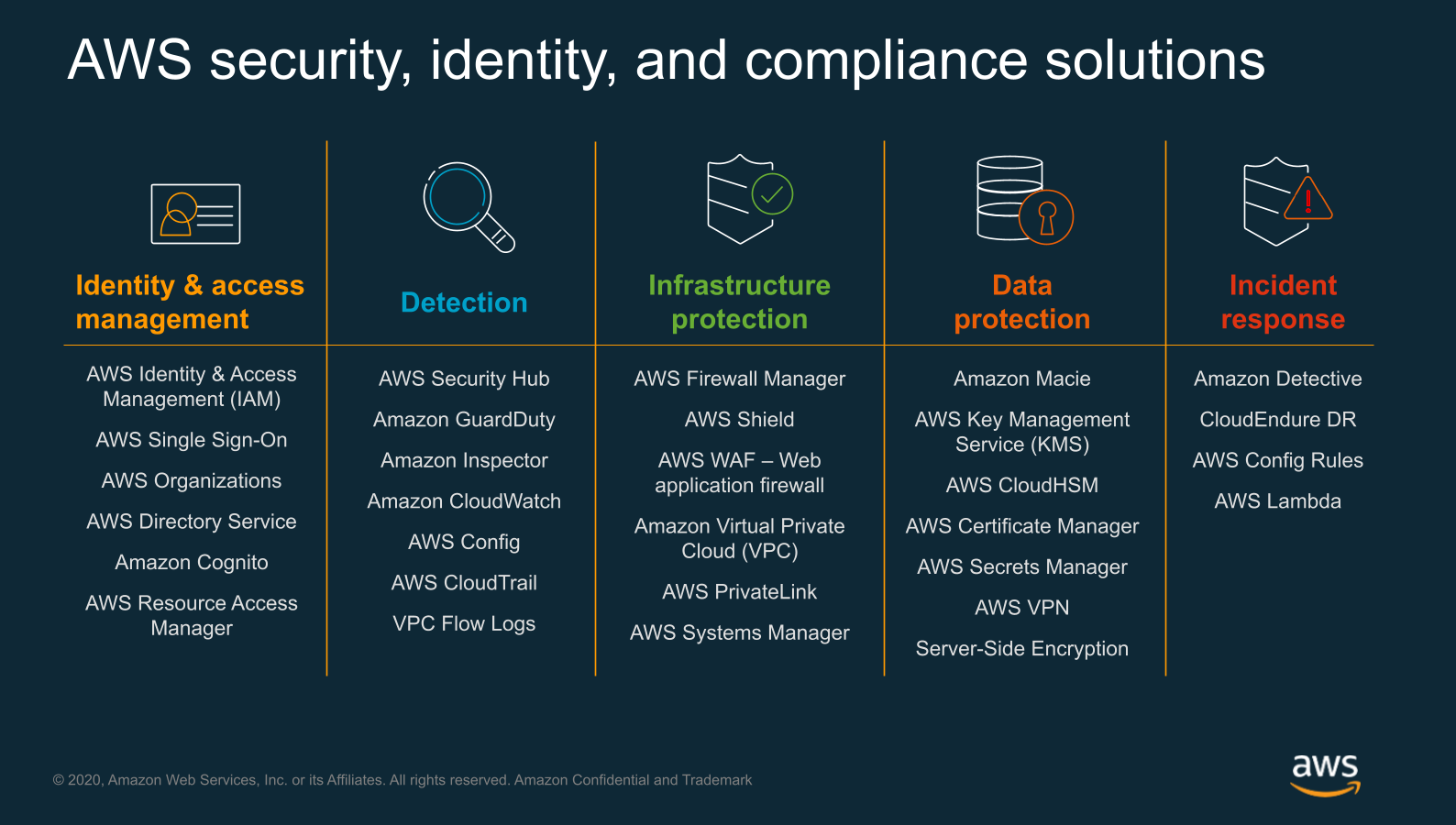
Lior began his presentation by discussing the uniqueness of the AWS infrastructure, and how its services, such as VPC, Lambda functions, DynamoDB and EC2 have many properties that have evolved over time and are specifically designed from the ground up.
From a security perspective, it is therefore critical to use security controls that natively interface with the specificity of these services and which have been designed with their particularities in mind.
Lior further discussed how AWS native security tools overlap with the NIST cybersecurity framework and fulfill the following five functions:
 During the webinar, the panelist invited the audience to participate in a series of polls, from which some interesting insights can be gathered.
During the webinar, the panelist invited the audience to participate in a series of polls, from which some interesting insights can be gathered.
First of all, about 85% of viewers seemed to misunderstand their responsibilities within the Shared Responsibility Model. 30% mentioned that misconfigurations and wrong setups posed the greatest risk to their cloud operation, while an additional 35% said that lack of qualified staff and know-how is their biggest operational challenge when protecting cloud workloads.
These numbers further emphasize the great benefit organizations gain from consulting a certified AWS Managed Service Provider Partner. AWS MSP Partners have the human resources, know-how and experience required to ensure airtight security.